Hacker Fundamentals: The Everyman's Guide to How Network Packets Are Routed Across the Web « Null Byte :: WonderHowTo
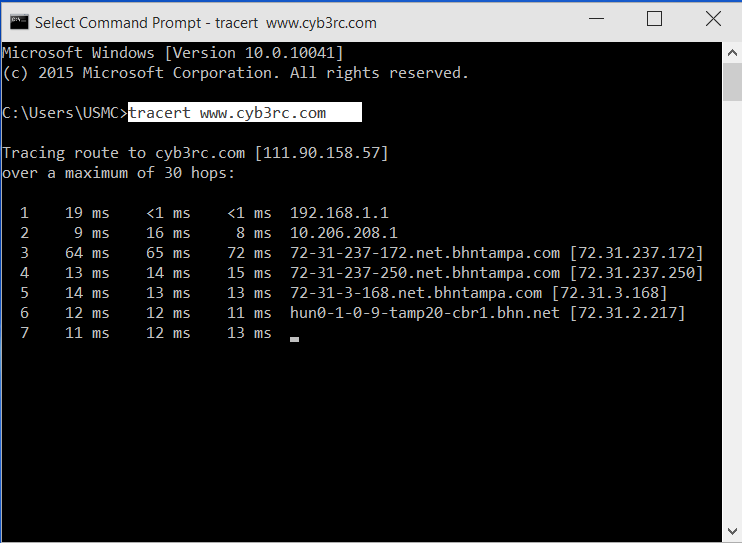
Hacker Fundamentals: The Everyman's Guide to How Network Packets Are Routed Across the Web « Null Byte :: WonderHowTo
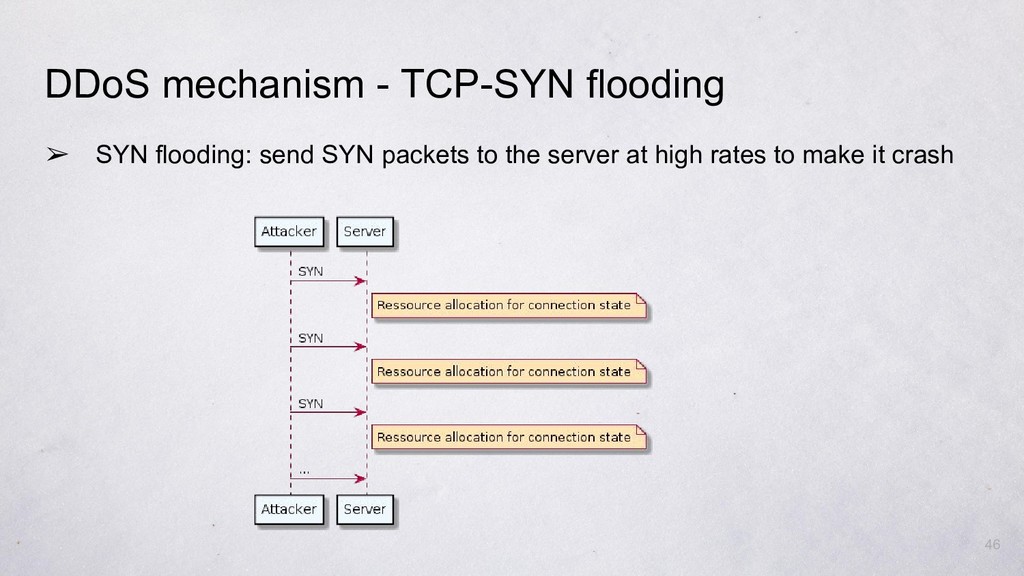
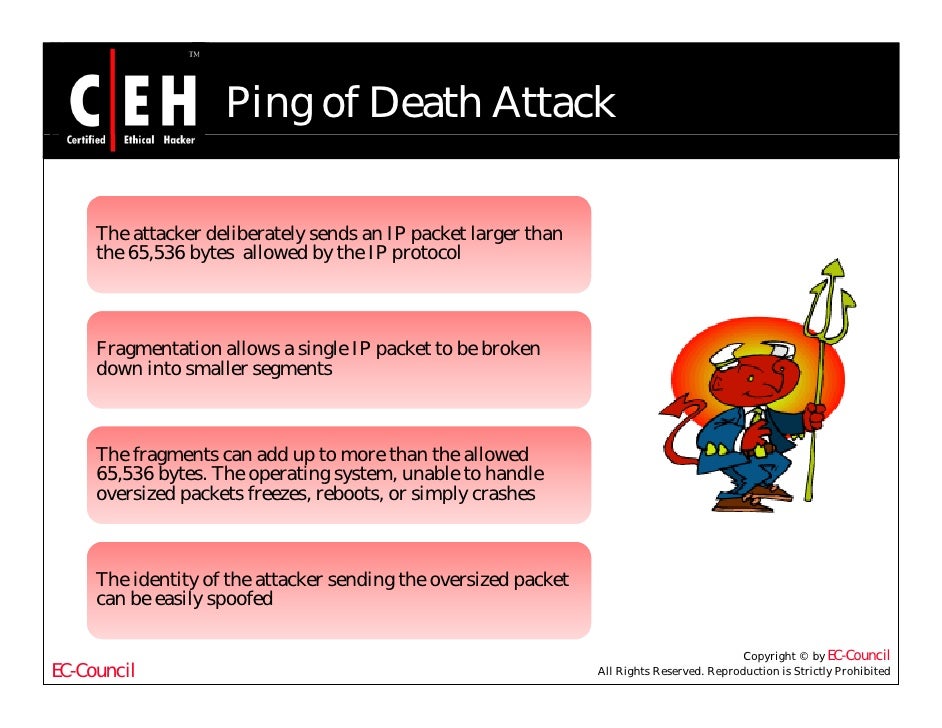
Types of Denial-of-Service Attacks | Staf of EC-Council - Ethical Hacking Student Courseware. Certidied Ethical Hacker-Exam 312-50 (EC-Council E-Business Certification Series)

How to hack a car — a quick crash-course | by Kenny Kuchera | We've moved to freeCodeCamp.org/news | Medium

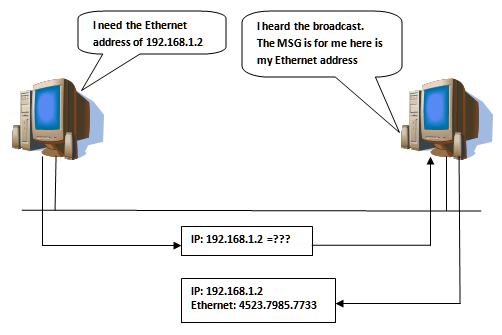
Hacker Fundamentals: The Everyman's Guide to How Network Packets Are Routed Across the Web « Null Byte :: WonderHowTo

Hacker Fundamentals: The Everyman's Guide to How Network Packets Are Routed Across the Web « Null Byte :: WonderHowTo

How to hack a car — a quick crash-course | by Kenny Kuchera | We've moved to freeCodeCamp.org/news | Medium